LINQ Workcell Networking and Cyber Security
last updated: 5 February 2024
At Automata, we are dedicated to ensuring your network is safe. This documentation outlines the measures we put in place to ensure this.
What hardware and software do we use and why?
Juniper Gateways and Switching
Our connection to your network starts with a Juniper Gateway device. We partner with Juniper because they provide us with the analytics and security needed to maintain stability on our platform. All hardware that we provision on site is backed by Junipers next day replacement service, this means that should any hardware have any issues we are able to swap it out in less than 24 hours. Additionally Juniper represents the highest standards in networking, meaning that it is constantly updated and improved to ensure it is safe and compliant with the latest industry standards.
Using Juniper also allows us to connect to your network in multiple different ways depending on your own cyber security requirements. This means we can connect to a DMZ, a dedicated VLAN, a DHCP allocated static IP, or put within a laboratory range. We utilise both NAT and SDwan architecture to ensure our bandwidth utilisation and outward traffic is kept to the bare minimum.
All of our hardware is provisioned in a zero trust fashion, this means that nothing works by default and has to go through a change management process before deployment.
Our workcells are architected using this to ensure that our instruments and robotics are secure and safe, that we retain full control over the network layer that all our devices communicate on is paramount for the way that our platform operates.
MiST AI Network Management
Controlling and orchestrating our network layer is MiST. MiST is a cloud based management application that allows us to remotely deploy, manage, monitor and report upon the network hardware within our LINQ Workcell.
We use MiST because it is able to provide us real-time usage analytics including latency and health. This means that our LINQ Workcell goes through constant improvement and allows for rapid diagnosis of any issues remotely without the need for on-site engineering. We are also able to identify damaged cables and connections.
MiST also is the best-in-breed when it comes to cyber security monitoring and prevention, we link MiST’s reporting directly to our SOC and our Threat Intelligence platform, meaning that in the event of a cyber security incident we are notified immediately and remediatory action is taken automatically.
The work we do on our network is also constantly backed up to the MiST system, this means that should the network suffer a hardware fault a replacement will be immediately provisioned once installed with no impact to service.
Finally, MiST’s management is non-intrusive and does not perform any decryption of data sent over our network, it contains no client data or data about the operations within the cell.
InTune Device Management
www.microsoft.com/en-gb/security/business/microsoft-intune
Due to the nature of some of the instruments used in labs we utilise Windows to provide a control plane to this hardware. We want to ensure that these devices are regularly updated and maintained. To do this we utilise Microsoft’s intune platform, meaning that we are able to push regular essential updates and provisioning scripts. We are also able to remote on-to hardware should there be an issue with hardware on-site.
Remote access is controlled via a 2-factor authentication system maintained by Automata, and requires at least 2 points of physical approval before access is granted. Our internal policies mean that passwords are constantly changed and maintained.
Intune also allows us to rapidly deploy replacement hardware should any device suffer a hardware fault we are able to restore it to service quickly without any need to reprovision the operating system on site.
Carbon Black End Point Protection
https://www.vmware.com/uk/products/carbon-black-endpoint
Cyber security is an area we take incredibly importantly, to do so we use the industry leader in threat intelligence Carbon Black made by VMware.
Carbon Black is intelligent threat detection and prevention, and is used as our main threat intelligence platform. It allows us to rapidly detect, trap and resolve cyber security issues and ensure that our workcells are protected from all forms of attack. It’s installed on all of our hardware by default.
Carbon Black utilises a code-less detection system, meaning that it can detect a wide variety of attacks and issues that would not normally be detected by standard anti-virus systems.
We will provide reports from Carbon Black regularly to clients so they can be safe in the knowledge that our hardware and software is secure.
Teleport Remote Access
Teleport is our remote access solution to allow to us to securely administer and enroll devices within our LINQ Workcells. It allows us to securely connect via a fully encrypted network path via AWS to our devices. This is protected by SSO and also can be added to an approval workflow so your internal teams can approve access.
Access and the links are not permanent and are only connected during support, we do not route any of your traffic over it at any time and this is blocked at a network level locally.
All access is fully audited, and all of our actions are recorded within this audit trails – this means that JIT access is fully safe, secure and also if needed controlled by you.
What our LINQ Workcell architecture looks like?
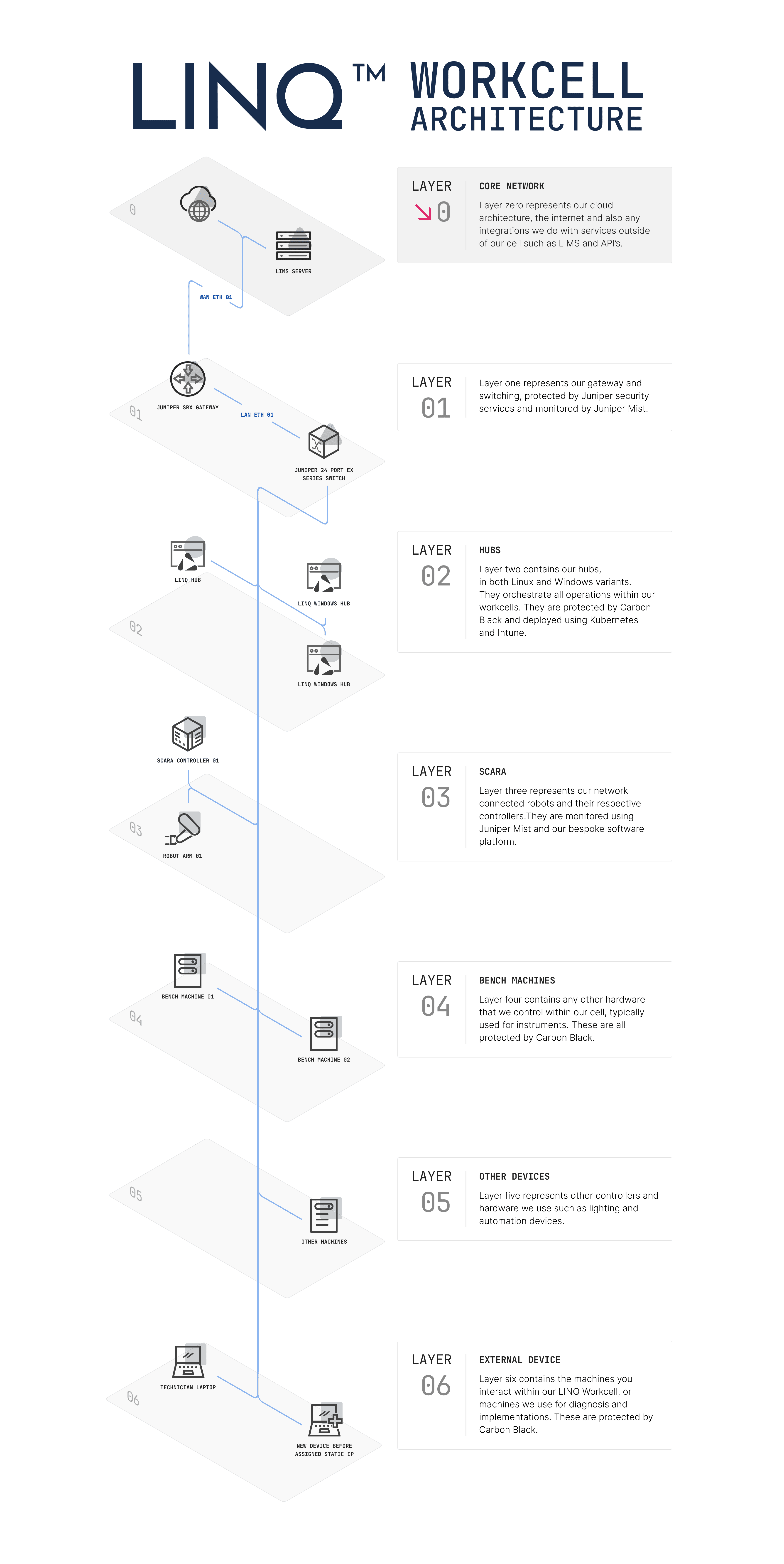
What protections do we take to ensure your network is safe?
Proactive Monitoring
All hardware and software in our workcells is constantly monitored for errors, issues and areas of improvement. This means that in many cases we will be aware of issues before they’ve been logged via our official support channels.
Monitoring information is collated from a variety of sources before being ingested into our threat and monitoring platform Carbon Black.
NAC/802.1x
Our network operates on a zero trust methodology, meaning that devices that aren’t approved for connection will not be allowed to access any data from on the network. We implement Junipers NAC solution for this, meaning that all devices must be pre-enrolled prior to connection.
Encryption and Storage
All data that is stored or transmitted on our networking infrastructure uses TLS 1.3 to transmit data securely, and we do not use any SSL decryption technology for packet inspection until it is at an endpoint.
Data is stored using AES-256 at a minimum at rest.
2 Factor Logins
All of our platforms require 2-factor authentication for login and require 2 physical means of authentication before access is approved. All passwords are secured safely within 1 password that is protected via a complex hash and 2 factor authentication in a separate system from the rest of our access planes.
What additional measures can we offer so you can monitor traffic on our network? (Span port, logs, read-only access)
Span Port
We understand that there is a need to investigate network hardware that is out of your team’s control, and to do this we are happy to provide a span port for a monitoring server if needed.
A Span port mirrors the communication from our devices to the rest of the network and allows you to perform deep packet inspection if required.
Log File Server
All of our network hardware is able to write system logs and store them for a period of time to a remote server of your choosing for ingest into your log processing server later. We’ll gladly provide DNS information so that you can map IP addresses to internal systems also.
Read Only Access to Mist
While we need to retain management of our MiST platform, we understand that you may want to periodically review the system or provide an API connection into your own Threat detection system. We will provision you access to the MiST system via 2-factor authentication login that you can use to grab what information you need from the network.
What processes do we follow to ensure our network is secure and robust?
Change Control
For all out-of-band alterations we follow strict CAB (Change advisory board) standards, meaning that any new implementations or workflow impacting changes go through multiple levels of internal approval and are booked at a time that is convenient for our end users.
Proactive Maintenance
All of our LINQ Workcells go through regular proactive maintenance, both remotely and on-site. This means that we identify problems before they become services impacting and develop improvements constantly.
Business Continuity
We actively participate in an internal business continuity plan that is regularly practiced and updated, this means that in the case of issues with any of our services we have multiple options available to ensure uptime and uninterrupted service.
Disaster Recovery
We have rigorous disaster recovery procedures in place as part of our continuity plan, that are supported by our technology partners.
Independent Review
All of our network and cyber security implementations are reviewed by an impartial 3rd party to ensure that we are always following industry best practices.
Contact our team
For questions or further information, please get in touch